Modern Data Protection & Recovery in a Multi-Cloud World
Organizations pursuing a data-first strategy must ensure that their data is always available, while being protected at all times. To achieve this, a modern data protection strategy is essential. This includes protection against ransomware.
Data and software form the basis of any digital business strategy. This fact – combined with the speed at which markets change – is driving companies to use more and more cloud services. For most of them, it’s not just about scalability or cost. It is also about being able to immediately use IT platforms and their state-of-the-art technologies and services to drive innovation.
In the data age, the cloud is therefore not a target, but an operating model. To do justice to the increased importance of data, such an operating model requires a data-first approach. This serves to anchor the data-oriented approach in the company and ensure that the data is secured, protected and available wherever and whenever it is needed.
Data backup is personal responsibility
The security of the data has the highest priority. Companies must ensure that they correspond to compliance and internal company regulations and data protection laws. An important decision also concerns the geographical location: May the data leave Switzerland or do customers assume that the data will remain within the country’s borders?

Regardless of whether data is stored on-premises or in a public cloud and which cloud service is used, a modern data protection strategy is more important than ever in multi-cloud environments.
This includes deciding where and in what form data is primarily stored and processed. Whether data archiving is necessary and what it looks like. Furthermore, the question must be answered whether additional data copies must be kept for peripheral systems. Based on the relevance of the data to be protected and its applications for business operations, the solution for business continuity and disaster recovery is then selected and the parameters for recovery point objective (RPO) and recovery time objective (RTO) are defined.
Data should be flexibly stored in the company’s own data center on data protection appliances designed specifically for this purpose or in the public cloud on virtual appliances. This ensures that the data is kept independent of location and public cloud providers. This reduces vendor dependency, minimizes risks and also makes it possible to use the cloud providers with the most economical offer in each case.
Increasingly important: Protection against ransomware attacks
An important component of a data protection strategy is protection against ransomware attacks. With the help of a few easy-to-implement immediate measures, business continuity can be ensured first. For example, modern on-premises solutions offer the possibility of creating an « Immutable Snapshot » several times a day according to business requirements. These logical copies make it possible to restore an environment to the state before the attack within seconds. Immutable Snapshots are themselves protected from attack because they can be defined as non-deletable. This means that even a system administrator cannot delete or overwrite these copies before a predefined time has elapsed.
However, these immediate measures do not protect against the complete loss of control over the primary and data protection systems. Companies whose business models rely heavily on the availability of IT systems should supplement these measures with an independent cyber recovery solution.
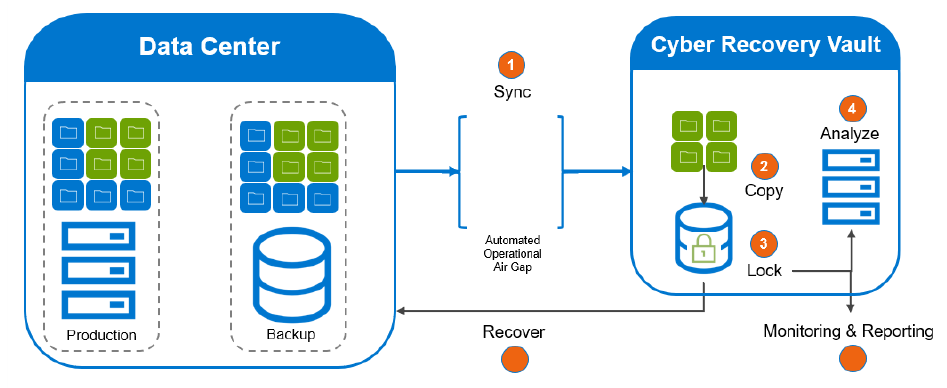
The cyber recovery solution duplicates the created data protection copies once a day to an isolated and completely independent system. Once the data transfer is complete, the system is isolated from the network to create an air gap. This prevents potential attackers from accessing the backup copies via the company network. Optionally, such a solution can be extended with CyberSense software. This offers full content indexing and uses modern machine learning algorithms to diagnose traces of corruption by ransomware, which can be used by the incident response team if necessary.
Data-driven technologies and multi-cloud environments offer companies an ideal foundation for their digital business applications. But only with a location-independent, state-of-the-art data protection & recovery solution can they achieve the level of security for their data that is Data First’s top priority.
