The Dell SonicWALL Threat Research Team gathers information from millions of firewalls, email security, and IPS solutions deployed in more than 200 countries. Our threat research team collects and shares information with 50 plus industry collaborations including WildList, AVIEN, PIRT, APWG, and Microsoft Active Protections Program (MAPP).
The threat research team brings 10+ years of security and malware research experience in collecting, analyzing, and creating countermeasures. The 2015 Dell Security Annual Threat Report summarizes what the team witnessed in 2014, provides guidance on emerging threats we should anticipate in the future, and recommends steps you can take protect your organization from these threats.
As organizations are contending with unprecedented challenges in combating cyber criminals, we notice that the sophistication and volume of attacks on enterprises are growing. The threat report identifies multiple findings, including three of particular note:
- A surge in point-of-sale (POS) malware
- A dramatic increase in encrypted traffic
- Growing attacks on SCADA systems.
Explosion of point-of-sale malware
There was a 300 percent increase in new POS malware countermeasures developed and deployed by Dell in 2014 over 2013. On a recent business trip outside the US, I noticed retailers asking me to enter a PIN when swiping my credit card. And now, this Chip and PIN technology is soon to be introduced in the U.S. When interacting with customers outside North America, the general perception is that U.S. companies seem to be willing to accept lower levels of security to provide convenience for their customers. And, as I would have predicted, the data indicates that the majority of POS hits targeted the U.S. retail industry; lack of strict security measures by the U.S. retail industry can be cited as one of the reasons for this phenomenon. The threat report provides multiple recommendations including isolating the network zone of the POS systems, restricting access to and from the system etc., apart from providing adequate training to employees accessing the systems.
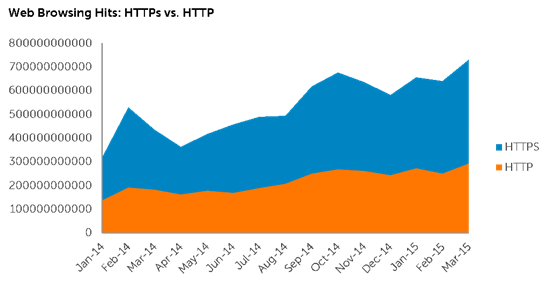
The rise of encrypted trafficOld stat analysts and pundits have been predicting an all encrypted Internet which theoretically will help guard our individual privacy rights against the intrusion of big government. Our data backs this up, showing a 109 percent increase in the volume of SSL and TLS encrypted Internet connections from the start of 2014 to the start of 2015. As of March 2015, our data shows that 60 percent of the billions of hits that our researchers see is HTTPS. We expect this trend to grow.
Though SSL/TLS provides privacy and offers secure exchange of information, it also allows a secret path for hackers to exploit security vulnerabilities. Most traditional firewalls don’t offer SSL decryption and in turn have no ability to inspect the encrypted traffic. This reminds me of Dan Geer’s key note at Black Hat 2014 where he noted, “… Freedom, Security, and Convenience — Choose Two”. Without divulging into the political sentiment expressed by Geer, Next-Generation Firewalls have the ability to inspect encrypted traffic offering both security and convenience without compromising the privacy of the users.
SCADA system threats
We also found that “Buffer overflow vulnerabilities” were the primary attack method on supervisory control and data acquisition (SCADA) systems. We noticed a 100 percent increase in attacks on SCADA controls targeted primarily in European and North American installations. We expect these attacks to grow as more of these aging systems get connected to the internet without proper security precautions such as restricting connecting IPs, disabling unused ports, etc.
Security is an ongoing process, the threat team works around the clock using manual and automated techniques to send real-time updates to Dell security devices. A subset of the security protection offered by Dell security solutions in 2014 includes:
- Blocked 1.68 trillion IPS attacks
- Stopped 4.2 billion malware attacks
- Released thirteen advisories addressing Microsoft security bulletins, including out-of-band zero-day advisories
- Covered Fourteen zero-day vulnerabilities
In addition to the above key findings and research, the Dell Security Annual Threat Report provides a comprehensive list of trends, telemetry data and preventive actions that organizations can use to take action. Click here to download the complete version of the report.