Thanks to ever changing privacy laws and increasing threats to personal and corporate data, encryption has become a critical tool in the computer security arsenal. Encryption ensures sensitive data can only be read by those authorized to see the information, regardless of where that data is stored. It’s easy to get wrapped up in the technical details when evaluating the strengths and weaknesses of a security solution, such as the long term debate over Full Disk Encryption (FDE) vs. File/Folder Encryption (FFE). While technical details are important, you have to step back to look at the big picture.
One of my favorite quotes from well-known cryptographer and security expert, Bruce Schneier, highlights the importance of designing security around the end user:
”The user's going to pick dancing pigs over security every time.”
Admit it…you looked at the dancing pig, right?
At first glance this may seem like just a funny observation on human nature, but it’s much more. There’s always a trade-off between usability and security and as important as security is, users will find a way around it if you get in their way. Clever and motivated end users put a special burden on the IT and security teams tasked with protecting sensitive and personal information. It’s common to find systems infiltrated via well-known vulnerabilities, months or even years after the issue was identified. Articles on many of the recent attacks against large retail and financial companies mention that there were alerts and other indicators from security software long before the attack was recognized.
The challenge security solution providers, like Dell, face is how not only protect against constantly evolving threats and end user driven security gaps, but also help ease the IT’s struggle to keep up. Here are a few ways Dell Data Protection | Encryption (DDP | E) is working to do this:
- DDP | E Personal Edition provides simple, locally managed encryption for local hard drives and external media. This is a great option for smaller organizations or individuals, many of whom may not realize they are also subject to privacy and compliance laws.
- Since one size does not fit all, medium to large organizations can choose the best encryption for their environment and manage it all from a single console, even if their needs differ across the organization.
- DDP | E software encryption is a great way to protect data on laptops, desktops, smartphones, removable media or in the cloud. We also manage policy and report on Microsoft BitLocker so organizations can bring all their encryption together.
- For users with high performance needs, Dell’s exclusive FIPS 140-2 Level 3 validated DDP | Hardware Crypto Accelerator offers hardware based encryption on select Latitude, OptiPlex and Precision systems. Self-Encrypting Drives are another hardware encryption option managed by DDP | E for organizations that don’t need the higher level of FIPS validation or external media encryption included with DDP | HCA.
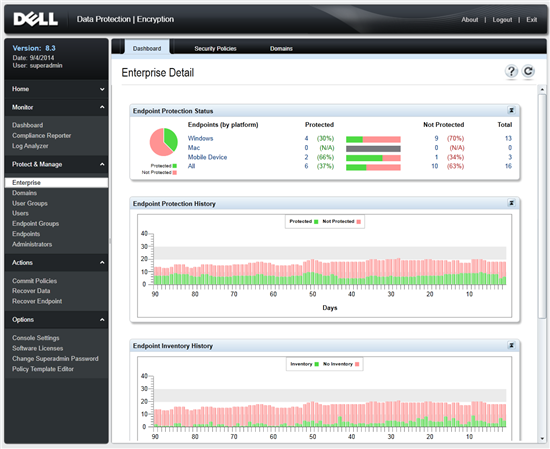
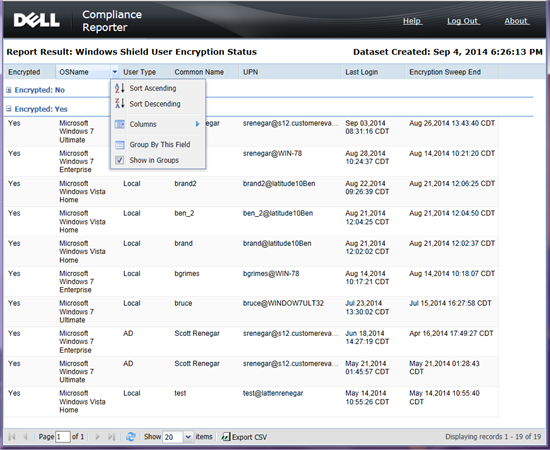
- DDP | E compliance reporting includes numerous templates that can be edited and scheduled. This allows IT to monitor their environment with high level and detailed views of all their encryption.
When the media talks about Dell Security the focus is often on how we ensure Dell customers have access to the Most Secure commercial PCs. While this is important, Dell Data Protection | Encryption was designed to embrace today’s heterogeneous environments and increasingly complex security and compliance requirements. In future blogs I’ll go into more detail about our unique multi-key encryption, external media encryption, and the DDP | HCA to show how Dell protects data wherever it goes, enables IT and end user productivity and allows users to work with their devices as they want to, even if that involves dancing pigs.
Dancing pigs image by Geoff Bosco via Creative Commons