All of us, whether we are browsing YouTube (the world’s second largest search engine); sending Gmail to someone across the globe; watching movies on Netflix; or socializing over Facebook, Twitter, and LinkedIn; are knowingly or unknowingly consuming cloud services. Similarly every organization—no matter the size and scale of operations—accessing software applications over the Internet, is consuming cloud services.
So it stands to reason that, as a consumer of cloud services, the obvious question that comes to my mind is: How do cloud service providers protect our applications and critical data in the cloud?
Last week, on the sidelines of Dell World 2015, I caught up with M. Brandon Swain, one of Dell’s Senior Security Consultants, to understand the industry’s view on cloud security.
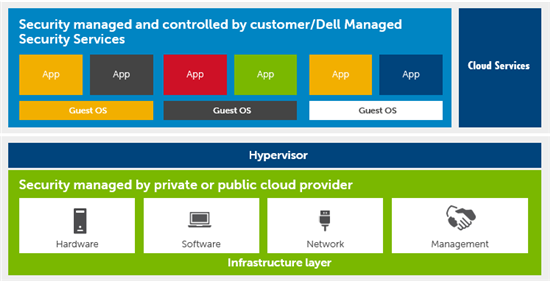
It was interesting to learn that both cloud service providers and cloud users (often called tenants) share the responsibility of providing adequate protection for cloud-based services. This shared responsibility has been acknowledged by leading standard bodies such as the National Institute of Standards and Technology, (NIST) and the Cloud Security Alliance, as well as major private and public cloud providers. In a nutshell, moving services (or workloads) to the cloud by simply swiping a credit card in the middle of the night (as the cloud providers often claim) opens up the door for potential security breaches and attacks. Remember that a U.S.-based credit card with a Card Verification Value (CVV) is sold for one to six dollars on the black market, and the price for personal identity numbers, with Social Security Numbers and dates of birth add an additional 14 to 18 dollars onto the price of credit card information.
Brandon also recommended the latest whitepaper on cloud security, which covers even more about the shared responsibility model in a cloud environment. This informative paper also highlights the innovative technologies used to safeguard critical data from external attacks and inside security breaches—thereby reducing the risk of lost, damaged or stolen information.
Critical security challenges when moving services to a cloud:
In my view, there are two critical security challenges when moving services or workloads to a cloud environment. The first is how to safely and securely access services in a cloud environment, while the second and bigger challenge is how to extend the enterprise security policies to the cloud.
On my way back from Dell World, I spent some time going through the whitepaper. It covers four key pillars of cloud security, and also articulates how Dell can help organizations take the complexity out of cloud deployment.
The four key pillars of cloud security:
- Host defense: Whether services are running on-premises or in the cloud, an organization needs to harden the virtual machine (VM) by using host-based protection (such as anti-virus, anti-spyware and host intrusion prevention system (IPS) software). This can be further complemented by providing web content filtering, and host log monitoring capabilities.
- Visibility and access control: Providing an added layer of protection in securing network infrastructure and workloads with help manage user accounts and provide authentication, authorization and accounting.
- Encryption: Encryption provides a new boundary that secures enterprise assets wherever they are. Encrypt if it’s relevant at the data, workload and transport levels.
- Operational simplification and visibility: Security needs to be consistent, transparent, and operationally simple to manage—whether workloads are running in the data center, in a private cloud or on a public cloud infrastructure.
Having a dialogue with a security expert cleared my doubts and clarified my thoughts. Reading the whitepaper also helped a great deal. Download the cloud security whitepaper.
For more information about cloud security, you might consider registering for our live webinar, titled “The secret sauce for cloud security” on Nov 4, to understand how Dell Security Services can help you analyze, design, deploy, manage, and extend enterprise security policies on your behalf—from on-premise, to private and public cloud.