Virtualized Active Directory is ready for Primetime!
In today’s technology climate, monitoring for changes should be part of the organization’s security culture. Your IT team knows the importance of securing the network against data breaches from external threats, however, data breaches from inside the organization represent nearly 70% of all data leaks[1].
Are you doing enough to prevent the data leaks? Enter Active Directory Domain Services (AD DS).
“Virtualize-First” Is the New Normal
Reasons to virtualize Active Directory Domain Controllers.
As the prominent directory service and authentication store, AD DS comprises the majority of network infrastructures, a business critical application (BCA). It provides the methods for storing directory data and making this data available to network users and administrators, thereby storing information about user accounts – names, passwords, phone numbers, etc. – and enables other authorized users on the same network to access this information.
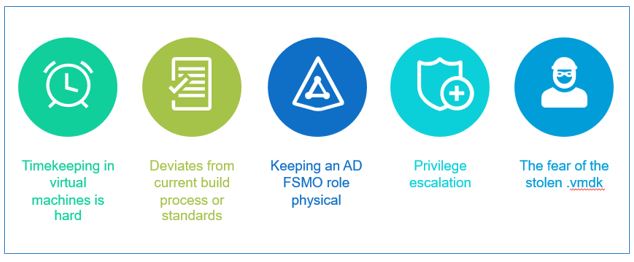
In much the same way that the criticality of AD DS differs in organizations, so does the acceptance of virtualizing this service. More conservative organizations choose to virtualize a portion of the AD DS environment and retain a portion on physical hardware. This proclivity stems from the complexity of timekeeping in virtual machines, deviation from current build processes or standards, the ability to keep an AD Flexible Single Master Operations (FSMO) role physical, privilege escalation, and fear of a stolen .vmdk.
But fear not!
The release of Windows Server 2012 (and Windows Server 2016) and its virtualization-safe features and support for rapid domain controller deployment alleviates many of the legitimate concerns that administrators have about virtualizing AD DS. VMware® vSphere® and our recommended best practices also help achieve 100 percent virtualization of AD DS.
Best Practices for Active Directory (AD) Availability
Active Directory is the cornerstone to every environment – when Active Directory comes to a halt, everything connected does too.
Since many domain controller virtual machines may be running on a single VMware ESXI host, eliminating single points of failure and providing a high-availability solution will ensure rapid recovery. VMware provides solutions for automatically restarting virtual machines. If a VMware ESXi goes down, VMware High Availability (HA) can automatically restart a domain controller virtual machine on one of the remaining hosts, preventing loss of Active Directory. Using configuration options, you can prioritize the restart or isolation status for individual virtual machines. VMware also allows you to specify a priority for restarting virtual machines. For example, it is important for domain controllers functioning as global catalog servers to be online before your Exchange Server environment initializes. It is always a best practice to set your domain controller virtual machines as high-priority servers.
Additionally, you can implement a script to restart a virtual machine via a loss-of-heartbeat alarm through vCenter. You can accomplish this using a script (available with the VI Perl Toolkit or the VMware Infrastructure SDK 2.0.1) and combined with VMware Distributed Resource Scheduler (DRS), ensure that domain controllers from the same domain always reside on different VMware ESXi hosts to prevent placing all the domain controllers in one basket. The anti-affinity rules let you specify which domain controllers must stay together and which must be separated.
For guidance, follow Microsoft Operations Master Role Placement Best Practices or Dell EMC’s recommended practices.
Achieving Active Directory (AD) Integrity in Virtual Environments
Performing consistent system state backups eliminates hardware incapability when performing a restore, and ensures the integrity of the Active Directory database by committing transactions and updating database IDs.
For success in implementing Active Directory in the virtual environment, you must ensure a successful migration from the physical environment to the virtual environment. Since Active Directory is heavily dependent on a transaction-based datastore, you must guarantee integrity by making sure there is a solid, reliable means of providing accurate time services to the PDC Emulator and other domain controllers throughout the Active Directory forest.
Network performance is another key to success in a virtual Active Directory implementation, since slow or unreliable network connections can make authentication difficult. Modifying DNS weight and priority to reduce load on the primary domain controller assists can help improve network performance. Because Active Directory depends on reliable replication, ensure continuity by using replmon to monitor it. Also, continue regular system state backups, and always restore from a system state backup. Virtual machines make it easy to move domain controllers; use VMware High Availability (HA) and VMware Distributed Resource Scheduler (DRS) so that no critical domain controllers are on a single host.
Practice the art of disaster recovery regularly. Finally, always go back and re-evaluate your strategies; monitor results for improvements and make adjustments when necessary.
Making Active Directory Confidential and Tamper-proof
Assessments in organizations that have experienced catastrophic or compromised events usually reveal they have limited visibility into the actual state of their IT infrastructures, which may differ significantly from their “as documented” states. These variances introduce vulnerabilities that expose the environment to compromise, often with little risk of discovery until the compromise has progressed to the point at which the attackers effectively “own” the environment.
Detailed assessments of these organizations’ AD DS configuration, public key infrastructures (PKIs), servers, workstations, applications, access control lists (ACLs), and other technologies reveal gaps in administrative practices, misconfigurations and vulnerabilities that, if remediated, could have prevented compromise and in extreme cases, prevented attackers from establishing a foothold in the AD DS environment.
See Microsoft’s Monitoring Active Directory for Signs of Compromise for further insights.

Summary
There are several excellent reasons for virtualizing Windows Active Directory. Virtualization offers the advantages of hardware consolidation, total cost of ownership reduction, physical machine lifecycle management, mobility and affordable disaster recovery and business continuity solutions. It also provides a convenient environment for test and development, as well as isolation and security.
Stay tuned for part II of this blog series where I’ll address proper time and synchronization with virtualized AD DC, replication, latency and convergence; preventing and remediating lingering objects, cloning, and disaster recovery.
Please reach out to your Dell EMC representative or checkout Dell EMC Consulting Services to learn how we can help you with virtualizing AD DS or leave me a comment below and I’ll be happy to respond back to you.
Sources
Virtualizing a Windows Active Directory Domain Infrastructure
Microsoft’s Avenues to Compromise
[1] Statista.com Data Breaches Recorded in the U.S. by Number of Breaches and Records Exposed
Related Blog
Best Practices for Virtualizing Active Directory Domain Controllers (AD DC), Part II


